File :
https://drive.google.com/file/d/0B1iFFi ... sp=sharing
aluigi wrote:Is it just one file or do you have more of them?
Anyway it's just a normal ZIP with a name_len (length of the filename) to which you have to substract 8:
http://aluigi.org/bms/lost_saga_iop.bms
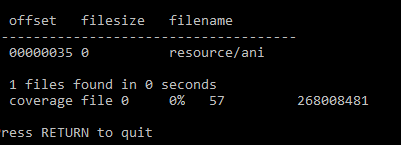
aluigi wrote:The files in this archive are probably encrypted because that data is not deflate.
aluigi wrote:rs.iop: offset 0x43, compressed size 0x5491, uncompressed size 0x8375.
That's definitely not deflate and I got no results from my scanner so, yes, it's encrypted.
aluigi wrote:Yeah, both server_patch.cfg.iop and lostsaga.exe.iop are not encrypted, while rs.iop is encrypted.
Maybe the encryption is used only for archives containing multiple files and not for single compressed files.
Ekey wrote:http://zenhax.com/viewtopic.php?p=117#p117
Code: Select all
set ZIP_PASSWORD string "Eg%^io03UT$Cvf921-!$"
goto -0x16
idstring "PK\x05\x06"
get disk_num short
get disk_start short
get central_entries short
get central_entries short
get central_size long
get central_offset long
get comm_len short
getdstring comment comm_len
for i = 0 < central_entries
goto central_offset
idstring "PK\x01\x02"
get ver_made short
get ver_need short
get flag short
get method short
get modtime short
get moddate short
get crc long
get comp_size long
get uncomp_size long
get name_len short
get extra_len short
get comm_len short
get disknum short
get int_attr short
get ext_attr long
get rel_offset long
savepos TMP
findloc name_len binary "PK"
math name_len - TMP
getdstring name name_len
savepos central_offset
goto rel_offset
idstring "PK\x03\x04"
get _ver short
get _flag short
get _method short
get _modtime short
get _moddate short
get _crc long
get _comp_size long
get _uncomp_size long
get _name_len short
get _extra_len short
getdstring name name_len
#getdstring extra extra_len
savepos offset
encryption zipcrypto ZIP_PASSWORD 1
if method == 0
Log name offset uncomp_size
else
if method == 8
ComType deflate
else
print "unsupported compression method %method%"
cleanexit
endif
CLog name offset comp_size uncomp_size
endif
encryption "" ""
next ialuigi wrote:@Ekey
I don't think that one is the key but feel free to check and fix it:Code: Select all
set ZIP_PASSWORD string "Eg%^io03UT$Cvf921-!$"
goto -0x16
idstring "PK\x05\x06"
get disk_num short
get disk_start short
get central_entries short
get central_entries short
get central_size long
get central_offset long
get comm_len short
getdstring comment comm_len
for i = 0 < central_entries
goto central_offset
idstring "PK\x01\x02"
get ver_made short
get ver_need short
get flag short
get method short
get modtime short
get moddate short
get crc long
get comp_size long
get uncomp_size long
get name_len short
get extra_len short
get comm_len short
get disknum short
get int_attr short
get ext_attr long
get rel_offset long
savepos TMP
findloc name_len binary "PK"
math name_len - TMP
getdstring name name_len
savepos central_offset
goto rel_offset
idstring "PK\x03\x04"
get _ver short
get _flag short
get _method short
get _modtime short
get _moddate short
get _crc long
get _comp_size long
get _uncomp_size long
get _name_len short
get _extra_len short
getdstring name name_len
#getdstring extra extra_len
savepos offset
encryption zipcrypto ZIP_PASSWORD 1
if method == 0
Log name offset uncomp_size
else
if method == 8
ComType deflate
else
print "unsupported compression method %method%"
cleanexit
endif
CLog name offset comp_size uncomp_size
endif
encryption "" ""
next i
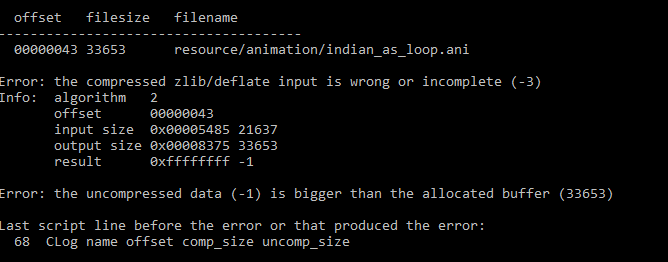
aluigi wrote:@Ekey
I don't think that one is the key but feel free to check and fix it:
aluigi wrote:The files in this archive are probably encrypted because that data is not deflate.
Ekey wrote:@rzlizfah - Just contact with author of this tool. Also as far as I know, for each local version of game client the passwords are different.
Ekey wrote:What the local version of client are you trying to unpack? Or you can upload IOP file, I'll check it myself